How IP Geolocation Tools Can Help You Prevent Phishing Attacks

Phishing’s roots are traceable as far back as the early 90s when a group of hackers known as the “Warez Community” launched an attack against America Online (AOL) users. In what was dubbed one the first phishing attacks (if not the first), the perpetrators developed a program to come up with randomly generated credit card numbers so they could create fake AOL accounts. They then used these accounts to spam users and scammed them into giving out personal information.
Decades after, the threat remains in use for one simple reason—phishing does work. But like many attack types, it has since evolved to take on more sinister forms or work on any kind of communication device. Regardless of innovations, though, phishing is preventable with the help of IP geolocation tools like an IP Geolocation API or a IP Geolocation Database.
Phishing: The Many-Fanged Threat
Over the years, phishing has matured and ever since affected individuals and organizations alike via multiple devices. Among its forms according to the equipment used are:
- Phishing: The original form of “phishing” was first introduced to computer users. Today, a new phishing site is launched every 20 seconds. It gets worse when the best practice of ensuring the websites you visit are secure no longer applies. Almost 75% of phishing sites now use HyperText Transfer Protocol Secure (HTTPS). And in just one week (6–13 April 2020), an employer as big as Google reportedly blocked as many as 18 million COVID-19-related phishing emails per day.
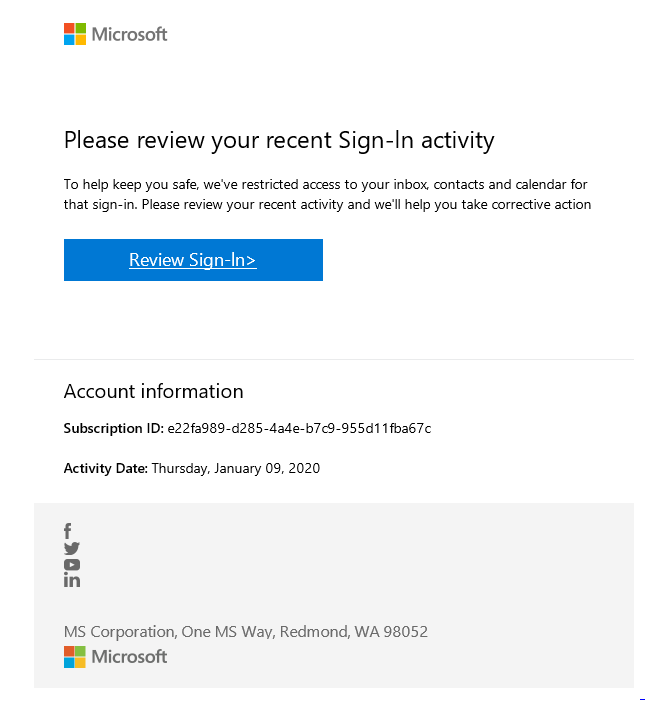
Here’s a sample phishing email that users should be wary of:
- Vishing: A term coined from a combination of “voice” and “phishing,” the threat occurs over Internet-enabled telephony service or voice over Internet Protocol (VoIP). The first of this phishing type was reported as far back as 2006. The attackers got users to think that their credit cards were used illegally. Today, vishers spoof company higher-ups to convince staff to transfer large sums of money into their accounts. Such was the case of a manager at an energy firm in the U.K. who lost £200,000 to attackers who used artificial intelligence (AI) to dupe him into thinking he was receiving orders from his boss.
- Smishing: A term coined from combining “short message service (SMS)” and phishing, smishing first appeared in early 2012. Back then, a German company reported the compromise of several of its clients’ private data through a smishing (also known as “SMShing”) attack. These days, any user can receive a mobile phone call or text message from a smisher asking him or her to divulge confidential information.
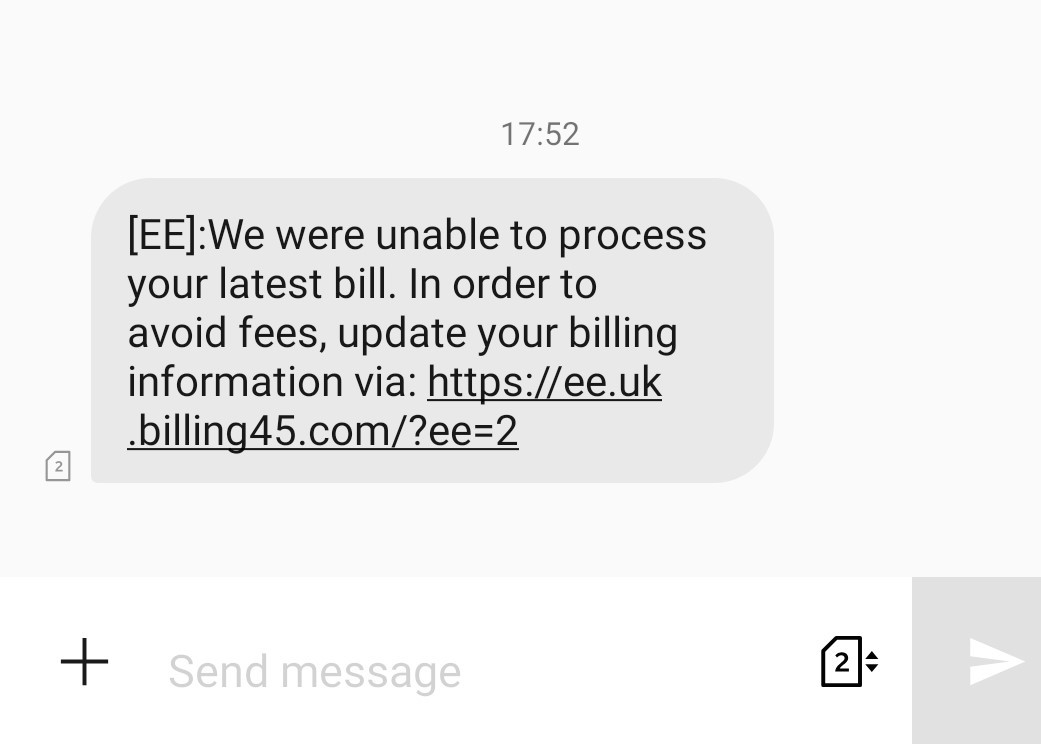
Here’s a common smishing message:
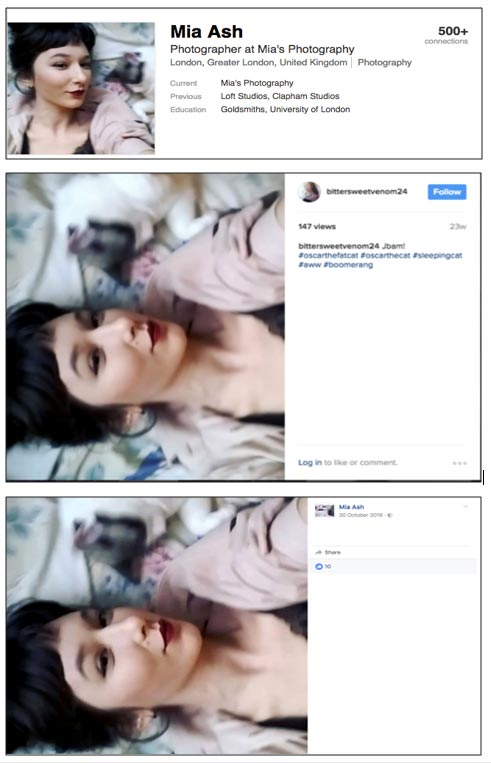
- Social media phishing: This type, of course, occurs on any social media platform. Sometimes shortened to “social phishing,” this type of phishing took flight as soon as social media platforms became mainstream. One example of this is the Mia Ash social phishing campaign that baited males into giving personal data to a fake Facebook user back in 2017.
Here’s the profile the attackers used:
As you can tell, cybercriminals keep up with the times and flock to where potential victims are. And because they know that they stand to earn more from victimizing large organizations, bigger cybercriminal rings also engage in spear phishing. One of its most successful forms is probably business email compromise (BEC). Also known as “email account compromise (EAC)” or “CEO fraud,” BEC scammers are said to have amassed more than $3.5 billion from victims in 2019.
These all prove how big a threat phishing remains despite better awareness and improved solutions. Can organizations and common end-users do something about it?
Can IP Geolocation Tools Help Combat Phishing?
The quick answer to that question is yes. Harnessing the power of an IP geolocation database or API can help, at least to some extent. Below are a few cases to demonstrate.
Case #1: Use an IP Geolocation Database to Set Alerts
Several sources of IP addresses to avoid can be found on the Internet and accessed free of charge. We obtained a list of malicious IP addresses from GitHub for this demonstration. It was in .txt format, which we converted into .csv so we can compare it with the sample IP Geolocation Data Feed we downloaded.
The 343,318 IP addresses in the sample blacklist for 11 June 2020 were cited for violations ranging from once up to 10 times by separate researchers. Here’s a breakdown in terms of citation volume:
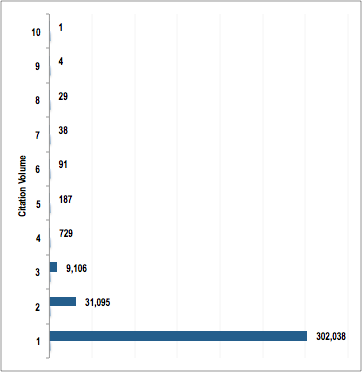
We looked at the IP addresses cited at least five times for malicious connections in the IP geolocation database to see if we could identify commonalities. We found a total of circa 350 malicious IP addresses. Our specific findings include:
- Netherlands topped the list of source countries or the locations where the majority (106, or 30%) of the malicious IP addresses originated. The U.S. (56), Germany (35), France (33), and China (27) followed at second to fifth place.
- By ISP, Netherlands-based ISP Joshua Peter McQuistan topped the list (51, or 15%) of malicious IP address managers. In second to fifth place, ISPs OVH SAS (38), DigitalOcean (19), Chinanet (18), F3 Netze e.V. (17) followed.
These findings hint at the need of closely monitoring the IP addresses managed by the leading ISPs in the top 5 countries. Integrating a geolocation database to serve as an intelligence source into security systems can help pinpoint IP addresses’ origins. Setting up an alert each time such an IP address appears can warn the security team to scrutinize the nature of the visit further.
Case #2: Integrate an IP Geolocation API to Spot Red Flags
Using the same dataset, we know that the IP address 171[.]25[.]193[.]77 was cited for malicious ties ten times. Consulting IP Geolocation API, we found that it’s ISP DFRI that manages the Sweden-based IP address.
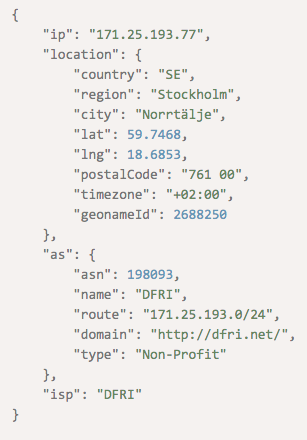
Upon checking, DFRI refers to the nonprofit organization Digital Freedom and Rights Association founded in 2011. It is a member of European Digital Rights. A web search for the keyword “DFRI” shows nothing untoward. Another search for the full organization name, however, includes a list of citations for malicious IP addresses.
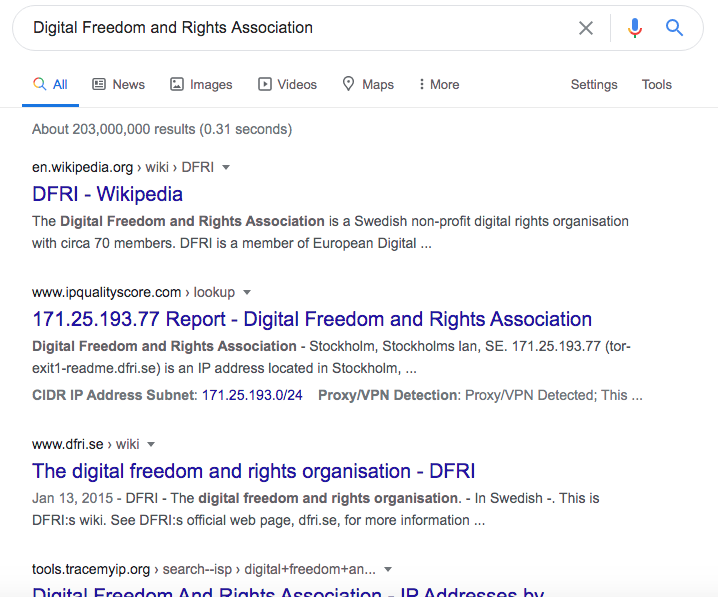
We looked into the report that talks about the malicious IP address (the same one we just checked on IP Geolocation API). We looked for more details as to why 171[.]25[.]193[.]77 was blacklisted and found that it is a spam-sending IP address and has connections to several malicious email addresses. It was also cited as a proxy or virtual private network (VPN) connection.
Integrating IP Geolocation API can help cybersecurity staff keep tabs on specific IP addresses that share details such as ISP and Autonomous System number (ASN) or route with others. The tool can issue alerts when commonalities between red-flagged IP addresses obtained from threat intelligence sources such as VirusTotal, Stop Forum Spam, and AbuseIPDB and incoming connections are spotted.
In some cases, an IP geolocation API query for an IP address would reveal connected domains. An example of this is the top 19 malicious IP address 193[.]70[.]12[.]219. According to IP Geolocation API, it resolves to the domain ns3061461[.]ip-193-70-12[.]eu.
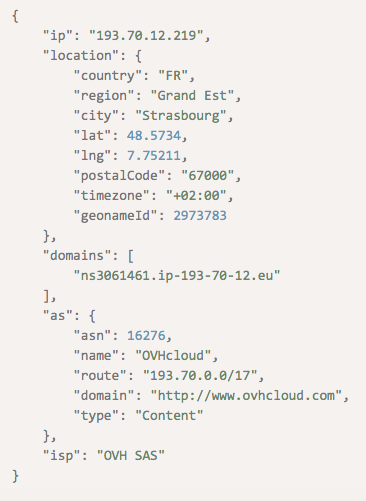
We searched for more information on the said domain and found that it was marked “suspicious” by VirusTotal by one engine.
---
As the two use cases showed, phishing attacks are stoppable with the help of early detection aided by IP Geolocation API and Data Feed. Malicious IP addresses can come in hundreds of thousands per day. And it’s just not possible to screen all incoming network connections manually.
But as we’ve shown, IP Geolocation Data Feed or API integration into security systems can help cybersecurity teams prioritize alerts and thwart phishing and other attacks before these can cause nearly irreparable harm.
---
Non-hyperlinked data sources:
- https://www.wandera.com/mobile-threat-landscape/
- https://docs.apwg.org/reports/apwg_trends_report_q4_2019.pdf
- https://cloud.google.com/blog/products/identity-security/protecting-against-cyber-threats-during-covid-19-and-beyond
- https://www.darkreading.com/vulnerabilities---threats/vishing-attacks-use-voip/d/d-id/1128151
- https://www.telegraph.co.uk/technology/2019/08/31/manager-energy-firm-loses-200000-fraudsters-use-ai-impersonate/
- https://bussinesshours.org/smishing-what-is-it-and-how-does-it-function-as-bait/
- https://www.zdnet.com/article/fbi-bec-scams-accounted-for-half-of-the-cyber-crime-losses-in-2019/
- https://raw.githubusercontent.com/stamparm/ipsum/master/ipsum.txt