How Cybercriminals Target You Based On Your Geolocation

IP geolocation is a crucial data point in the business sector. Knowing the location of website visitors and potential customers, for instance, allows organizations’ marketing teams to create targeted campaigns that are more effective than larger ones. Email and website content can be further personalized based on a target’s IP geolocation. Besides, IP geolocation data strengthens a company’s threat intelligence and cybersecurity programs.
While location-based targeting works well in marketing, advertising, cybersecurity, and other business processes, it also serves its purpose for cybercriminals. Location-based cyberattacks exist, too. In this post, we explored some of the ways that cybercriminals target users based on their location.
Target Profiling: Where You Are Matters
Some people may ask if physical location truly matters, at least, in terms of cyber risks. Shouldn’t the threats be the same for all users connected to the Internet? The answer is no. Cybercriminal groups tend to create victim profiles the same way that advertisers create target market profiles. And IP geolocation data plays a vital role in what type of attack and weapon threat actors will use against you.
Sweden: Trusting and Wealthy
In Sweden, for example, one of the most prevalent forms of cyber threats is ‘vishing’, or voice call phishing. Someone in the guise of a representative of a reputable company calls a victim to offer technical support. As part of the process, the caller requests a remote connection to the victim’s computer, allowing the cybercriminal to steal sensitive information or plant a piece of malware. Other criminals pretend to be representatives of banks and can therefore convince victims to share confidential information.
With the IP addresses of target victims, cybercriminals can gather more details, as seen in the screenshot from IP Geolocation API below.
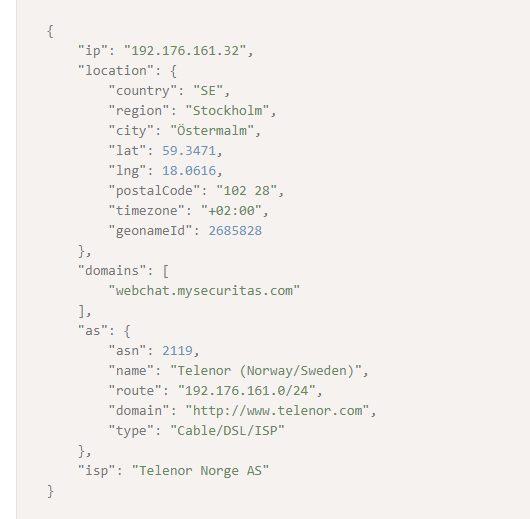
Aside from the victim’s location, threat actors can also confirm if the user indeed works for their target organization. IP Geolocation API revealed, for instance, that the IP address 192[.]176[.]161[.]32 is associated with the domain webchat[.]mysecuritas[.]com. If the cybercriminals are looking to target MySecuritas, they will know that they can use the IP address they obtained.
While vishing and phishing are not unique to Sweden, these are two of the country’s primary concerns. Why is that so? Cybercriminals do their homework, of course. Based on the World Value Survey, for instance, Sweden came only second to Norway in terms of having trusting people. Some 63.76% of the Swedish population agreed that “most people can be trusted.” Other factors would play a role also, such as the fact that the country is rich and the Swedes are the fifth most prosperous people in the world. That would translate into more significant financial gains for cybercriminals.
Brazil: Cautious Yet Reliant on Unsecure Public Networks
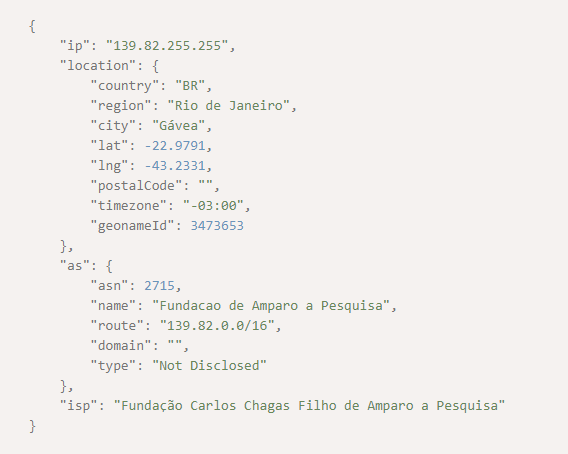
In Brazil, where only 6.53% of the population said that most people could be trusted, however, you may seldom find vishing as a go-to attack vector. Instead, cybersecurity issues there would initially involve malicious browser extensions and plug-ins. Public wireless networks could also serve as entry points for cybercriminals, as most of the country’s adult population rely on these for their Internet connection. Since threat actors know that Brazilians will rarely trust someone calling them out of the blue, they resort to sneakier methods and hide behind seemingly innocent browser plugins and unsecured public Wi-Fi.
Threat actors know that Rio de Janeiro is among the major cities in Brazil that has free wireless network connections. It has 7,243 free Wi-Fi hotspots. One of those hotspots may well have the IP address 139[.]82[.]255[.]255. And so, cybercriminals can launch their attacks based on that data point. Plotting the latitude and longitude returned by IP Geolocation API, for one, could point threat actors to a specific area within the city.
Japan: Elderly and Trusting
Some 28.2% of Japan’s population is 65 years of age or older. As such, the country has one of the most aged people in the world, along with Italy and Finland. Japan’s population is also mostly wealthy. Consequently, threat actors have been targeting the country through money transfer scams. In this scenario, a criminal will tell the victim that a family emergency has occurred and that he or she needs to transfer some money immediately.
In 2019, police set a new record of 9,542 such cases, most of which involved money transfer scams targeting the elderly. A 70-year-old woman in Tokyo was one of the victims. She lost ¥1.4 million or around US$13,000.
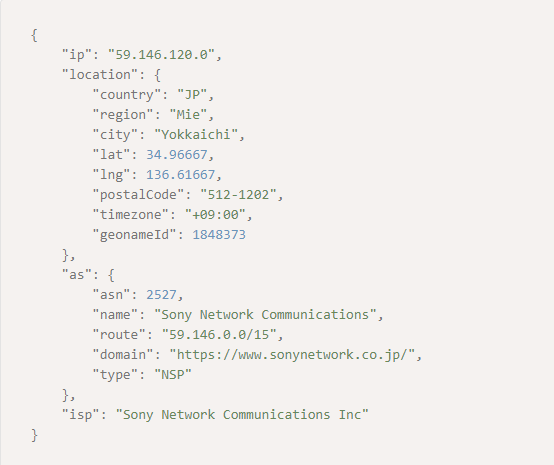
With IP Geolocation API, it’s easy to see how threat actors can target the vulnerable. The IP address 59[.]146[.]120[.]0 will tell criminals that the user is from Yokkaichi, Mie, Japan, where there are several nursing homes for the elderly.
We could go on and cite more countries to prove the point that your physical location matters to cybercriminals. IP geolocation data is indeed instrumental to threat actors.
Location-Based Malware
When cybercriminals develop malware, they do so with a target profile and IP geolocation in mind. In Brazil, for instance, where most Internet users use Google Chrome and Mozilla Firefox, cybercriminals create malware plugins specific to these browsers. It’s no different from car manufacturers that build right-hand driving cars for the U.K. and other countries whose drivers stay on the left side of the road.
As such, the cybersecurity landscape consists of different malware specifically designed for a particular region. We cite some of these malware below.
Ransomware
Cybercriminals usually target wealthy nations in ransomware attacks. After all, the citizens and organizations of these countries are more likely to pay them. In the U.S., for instance, 74% of small business owners that employ 150–250 employees would be willing to pay to recover their data.
An example of location-based ransomware is Locky. The ransomware renames all of the victim’s files and gives them the extension .locky after encryption. Locky’s ransom notes also come in Danish, Chinese, and Portuguese. Interestingly, if the ransomware detects that the victim’s preferred language is Russian, it deletes itself from the infected device.
Banking Trojans
Malware meant for the banking and financial sectors are also geo-targeted. For example, the Dridex banking Trojan has been targeting U.S. bank accounts after having done with European banks. Germany, on the other hand, saw an influx of DanaBot attacks in the previous year.
ZBot, an Android banking malware similar to the Zeus Trojan, started targeting Russian users in 2015. However, we’ve seen reports of its presence not long after in Australia, Canada, Italy, Spain, the U.S., and the U.K.
---
IP geolocation data, like any other form of intelligence, is double-edged. Users can benefit from that information, such as when providing personalized content and hassle-free e-commerce experiences to customers. On the other hand, threat actors can use the same IP geolocation data to launch geo-targeted attacks by using location-based malware.
Since there’s no one way to control and predict the actions of cybercriminals, infosec teams can keep up by making sure that their networks are well-protected from malware intrusion. Training their staff to recognize all forms of phishing and other attacks is also beneficial since sometimes, unknowing employees could be the weakest link in the cybersecurity chain.